What is a crypto honeypot and why is it used?
Smart contracts programs across a decentralized network of nodes can be executed on modern blockchains like Ethereum. Smart contracts are becoming more popular and valuable, making them a more appealing target for attackers. Several smart contracts have been targeted by hackers in recent years.
However, a new trend appears to be gaining traction; namely, attackers are no longer looking for susceptible contracts but are adopting a more proactive strategy. Instead, they aim to trick their victims into falling into traps by sending out contracts that appear to be vulnerable but contain hidden traps. Honeypots are a term used to describe this unique sort of contract. But, what is a honeypot crypto trap?
Honeypots are smart contracts that appear to have a design issue that allows an arbitrary user to drain Ether (Ethereum’s native currency) from the contract if the user sends a particular quantity of Ether to the contract beforehand. However, when the user tries to exploit this apparent flaw, a trapdoor opens a second, yet unknown, preventing the ether draining from succeeding. So, what does a honeypot do?
The aim is that the user focuses entirely on the visible weakness and ignores any signs that the contract has a second vulnerability. Honeypot attacks function because people are frequently easily deceived, just as in other sorts of fraud. As a result, people cannot always quantify risk in the face of their avarice and assumptions. So, are honeypots illegal?
How does a honeypot scam work?
In crypto cyber attacks like honeypots, the user’s cash will be imprisoned, and only the honeypot creator (attacker) will be able to recover them. A honeypot usually works in three stages:
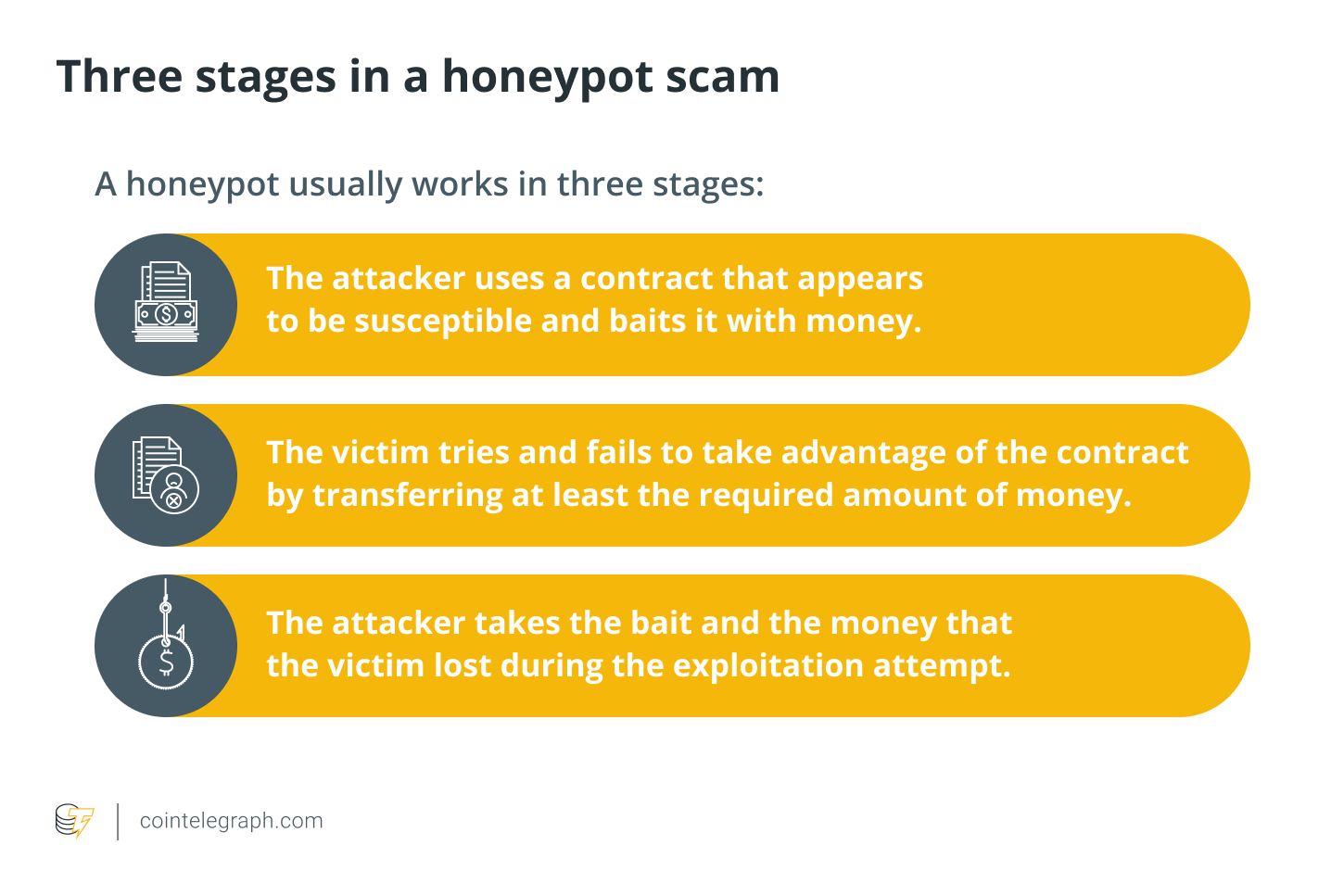 To set up honeypots in Ethereum smart contracts, an attacker does not need any specific skills. An attacker, in reality, has the same skills as a regular Ethereum user. They only need the money to set up the smart contract and bait it. A honeypot operation, in general, consists of a computer, programs and data that mimic the behavior of a real system that might be appealing to attackers, such as Internet of Things devices, a banking system, or a public utility or transit network.
To set up honeypots in Ethereum smart contracts, an attacker does not need any specific skills. An attacker, in reality, has the same skills as a regular Ethereum user. They only need the money to set up the smart contract and bait it. A honeypot operation, in general, consists of a computer, programs and data that mimic the behavior of a real system that might be appealing to attackers, such as Internet of Things devices, a banking system, or a public utility or transit network.
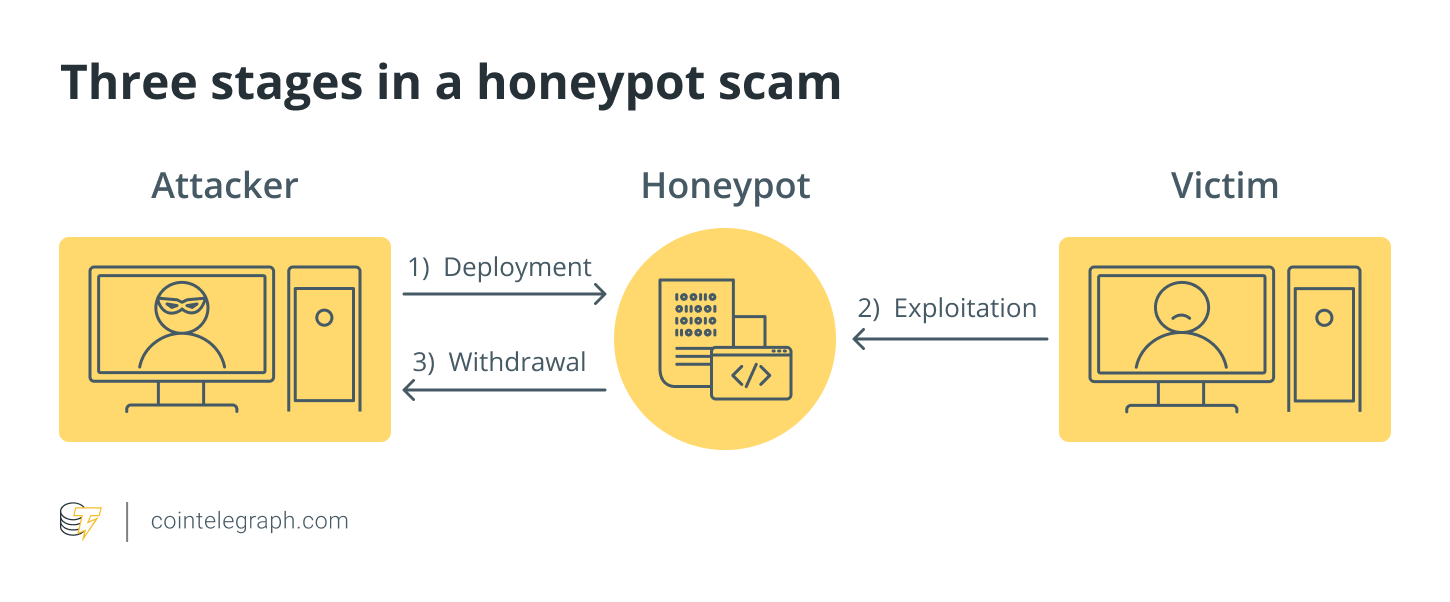 Even though it looks like a part of the network, it is isolated and monitored. Because legitimate users have no motive to access a honeypot, all attempts to communicate with it are regarded as hostile. Honeypots are frequently deployed in a network’s demilitarized zone (DMZ). This strategy separates it from the leading production network while keeping it connected. A honeypot in the DMZ may be monitored from afar while attackers access it, reducing the danger of a compromised main network.
Even though it looks like a part of the network, it is isolated and monitored. Because legitimate users have no motive to access a honeypot, all attempts to communicate with it are regarded as hostile. Honeypots are frequently deployed in a network’s demilitarized zone (DMZ). This strategy separates it from the leading production network while keeping it connected. A honeypot in the DMZ may be monitored from afar while attackers access it, reducing the danger of a compromised main network.
To detect attempts to infiltrate the internal network, honeypots can be placed outside the external firewall, facing the internet. The actual location of the honeypot depends on how intricate it is, the type of traffic it wants to attract and how close it is to critical business resources. It will always be isolated from the production environment, regardless of where it is placed.
Logging and viewing honeypot activity provides insight into the degree and sorts of threats that a network infrastructure confronts while diverting attackers’ attention away from real-world assets. Honeypots can be taken over by cybercriminals and used against the company that set them up. Cybercriminals have also used honeypots to obtain information on researchers or organizations, serve as decoys and propagate misinformation.
Honeypots are frequently hosted on virtual machines. For example, if the honeypot is compromised by malware, it can be rapidly restored. For example, a honeynet is made up of two or more honeypots on a network, whereas a honey farm is a centralized collection of honeypots and analysis tools.
Honeypot deployment and administration can be aided by both open source and commercial solutions. Honeypot systems that are sold separately and honeypots that are combined with other security software and advertised as deception technology are available. Honeypot software may be found on GitHub, which can assist newcomers in learning how to utilize honeypots.
Types of honeypots
There are two types of honeypots based on the design and deployment of smart contracts: research and production honeypots. Honeypots for research collect information on attacks and are used to analyze hostile behavior in the wild.
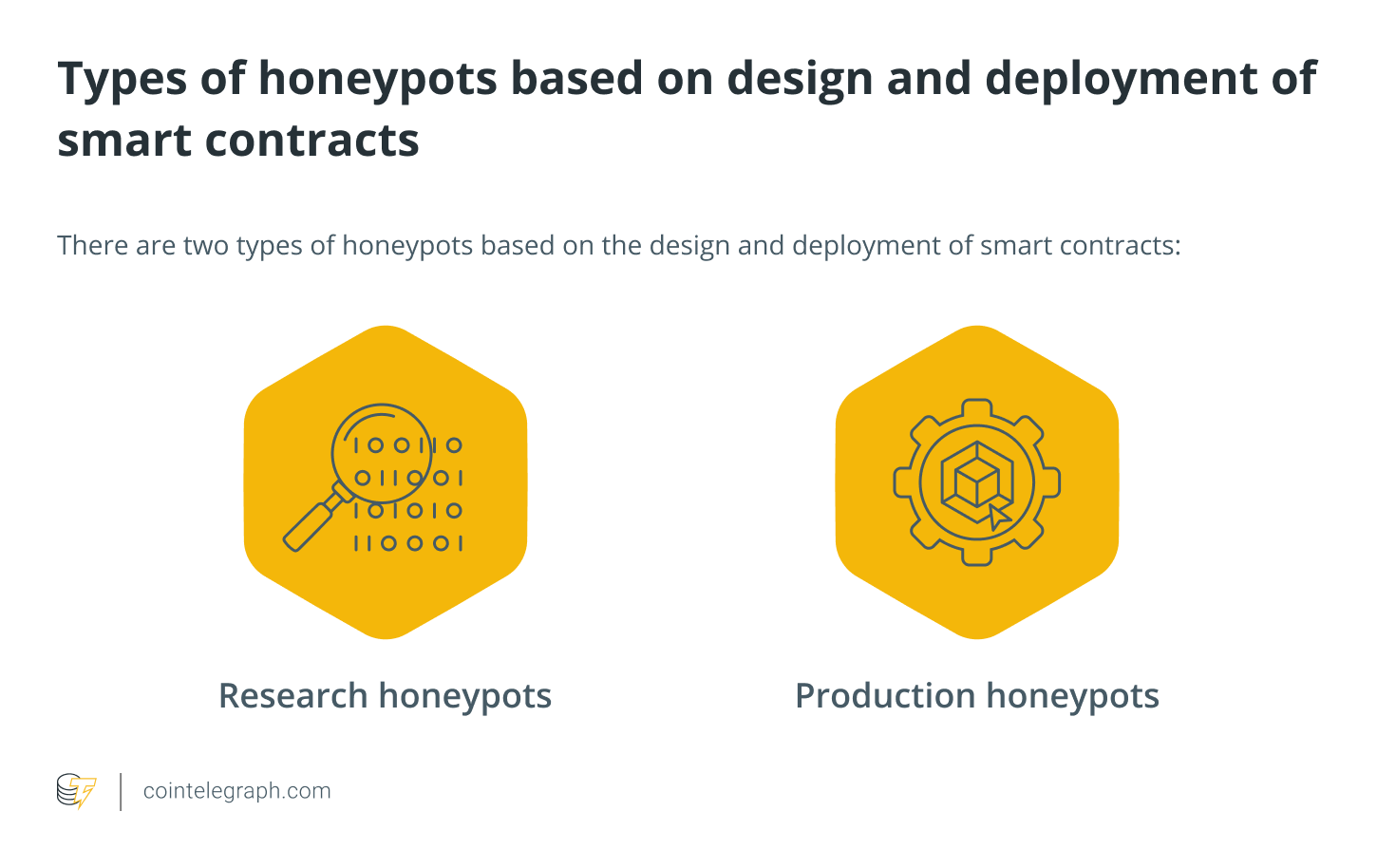 They acquire information on attacker tendencies, vulnerabilities and malware strains that adversaries are currently targeting by looking at both your environment and the outside world. This information can help you decide on preventative defenses, patch priorities and future investments.
They acquire information on attacker tendencies, vulnerabilities and malware strains that adversaries are currently targeting by looking at both your environment and the outside world. This information can help you decide on preventative defenses, patch priorities and future investments.
On the other hand, production honeypots are aimed at detecting active network penetration and deceiving the attacker. Honeypots provide extra monitoring opportunities and fill in common detection gaps that surround identifying network scans and lateral movement; thus, obtaining data remains a top responsibility.
Production honeypots run services that would typically run in your environment alongside the rest of your production servers. Honeypots for research are more complicated and store more data types than honeypots for production.
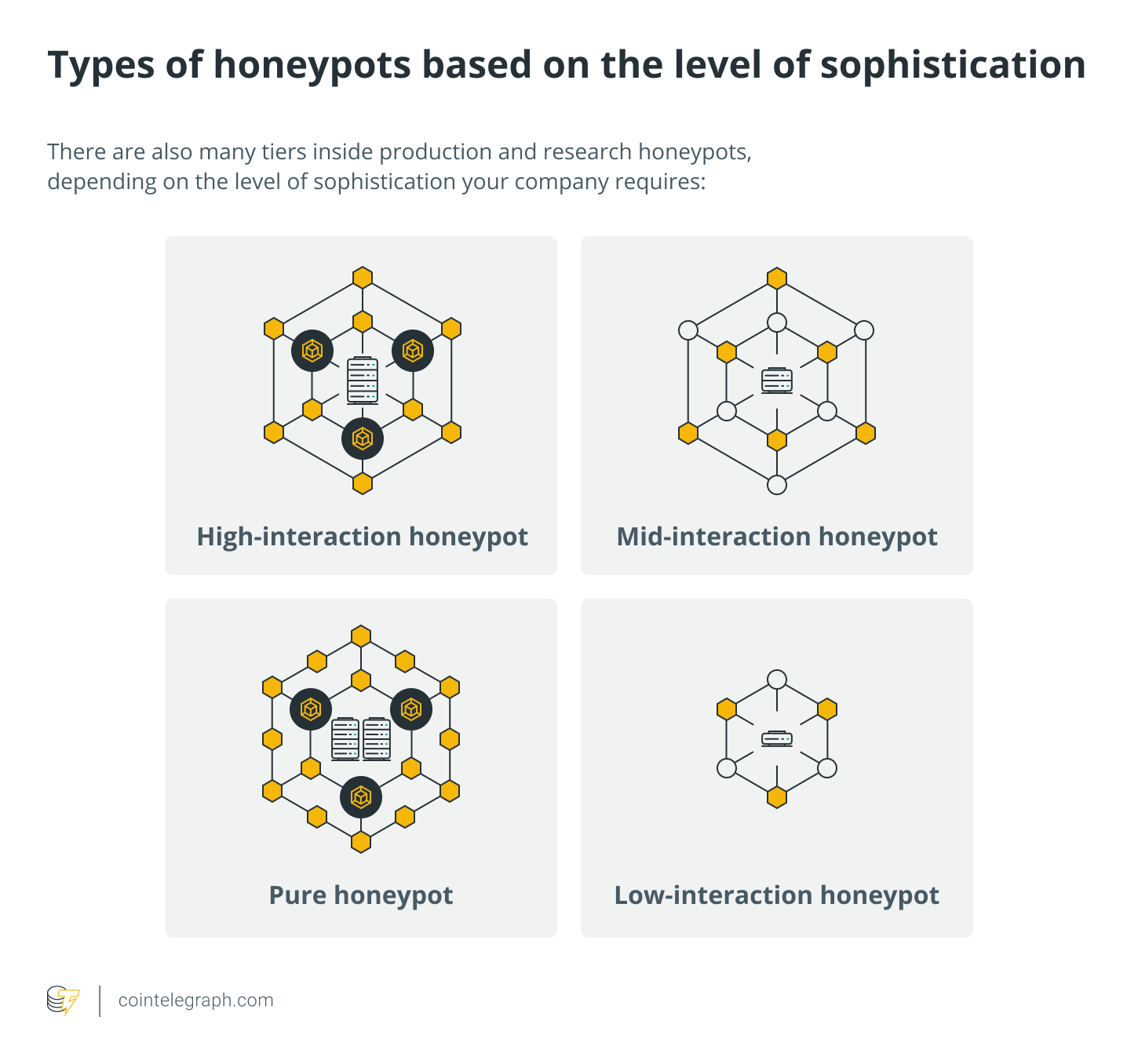
There are also many tiers inside production and research honeypots, depending on the level of sophistication your company requires:
The deploying company can observe attacker habits and strategies using this honeypot form. High-interaction honeypots need a lot of resources and are difficult to maintain, but the results can be worth it.
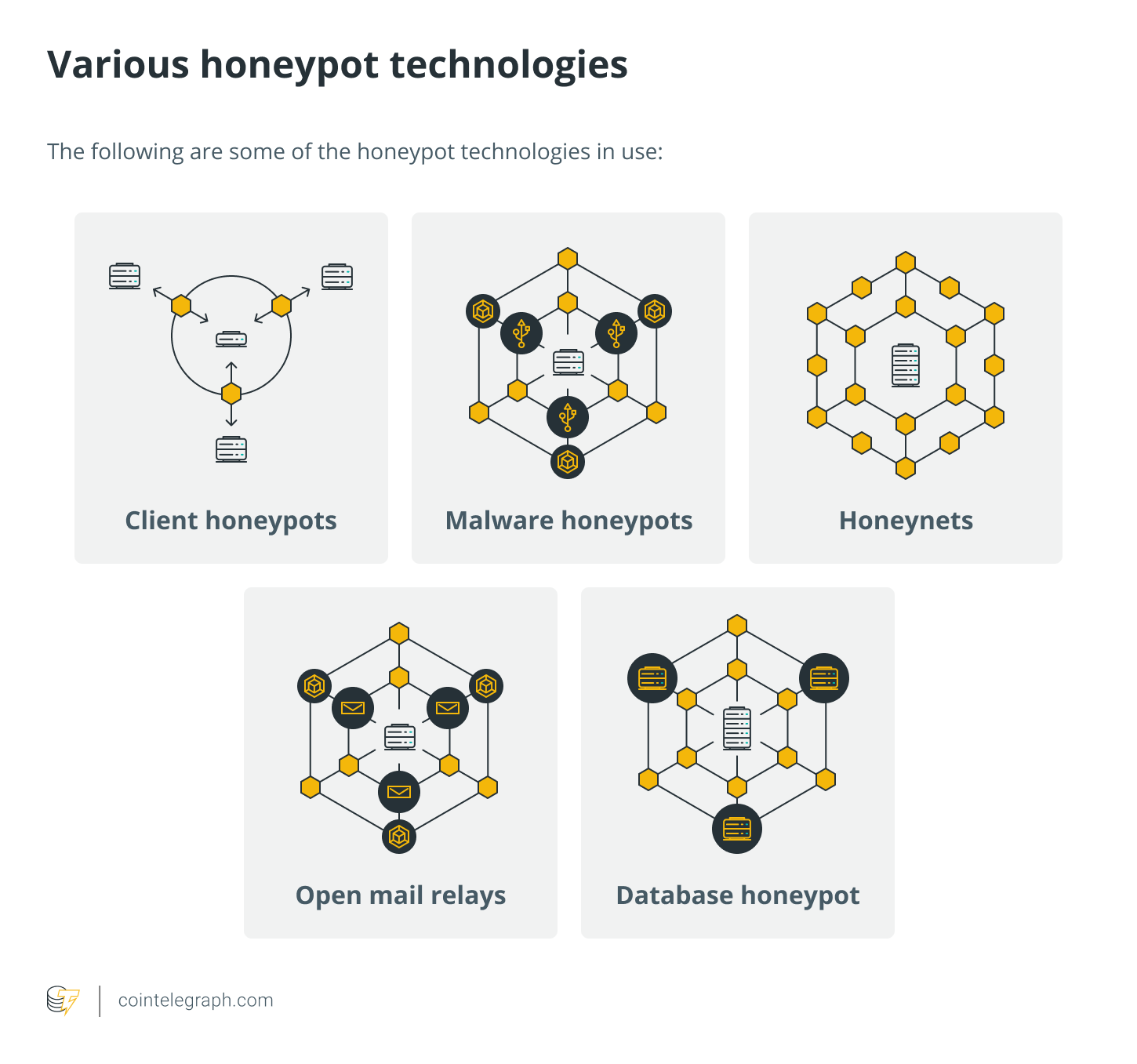
Several honeypot technologies
The following are some of the honeypot technologies in use:
How to spot a crypto honeypot?
Examining the trade history is one technique to recognize a honeypot crypto fraud. A cryptocurrency should generally allow you to buy and sell it whenever you desire. There will be a lot of buys for the coin in a honeypot scam, but people will have a hard time selling it. This indicates that it is not a legitimate coin, and you should avoid it.
Moreover, the data science approach based on the contract transaction behavior can be used to classify contracts as honeypots or non-honeypots.
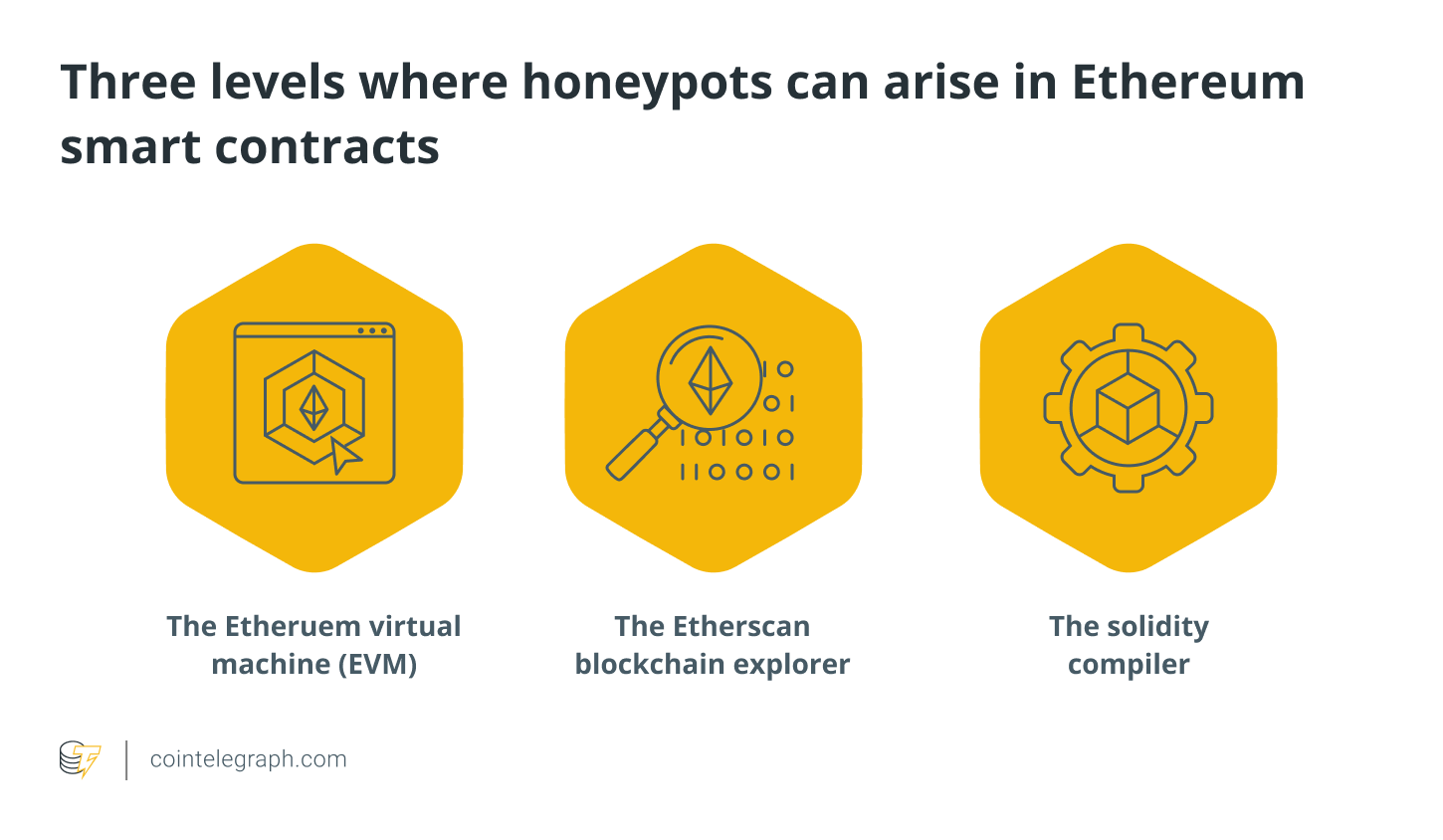
Where can honeypots arise in Ethereum smart contracts?
Honeypots might appear in three different areas of Ethereum smart contracts implementation. These are the three levels:
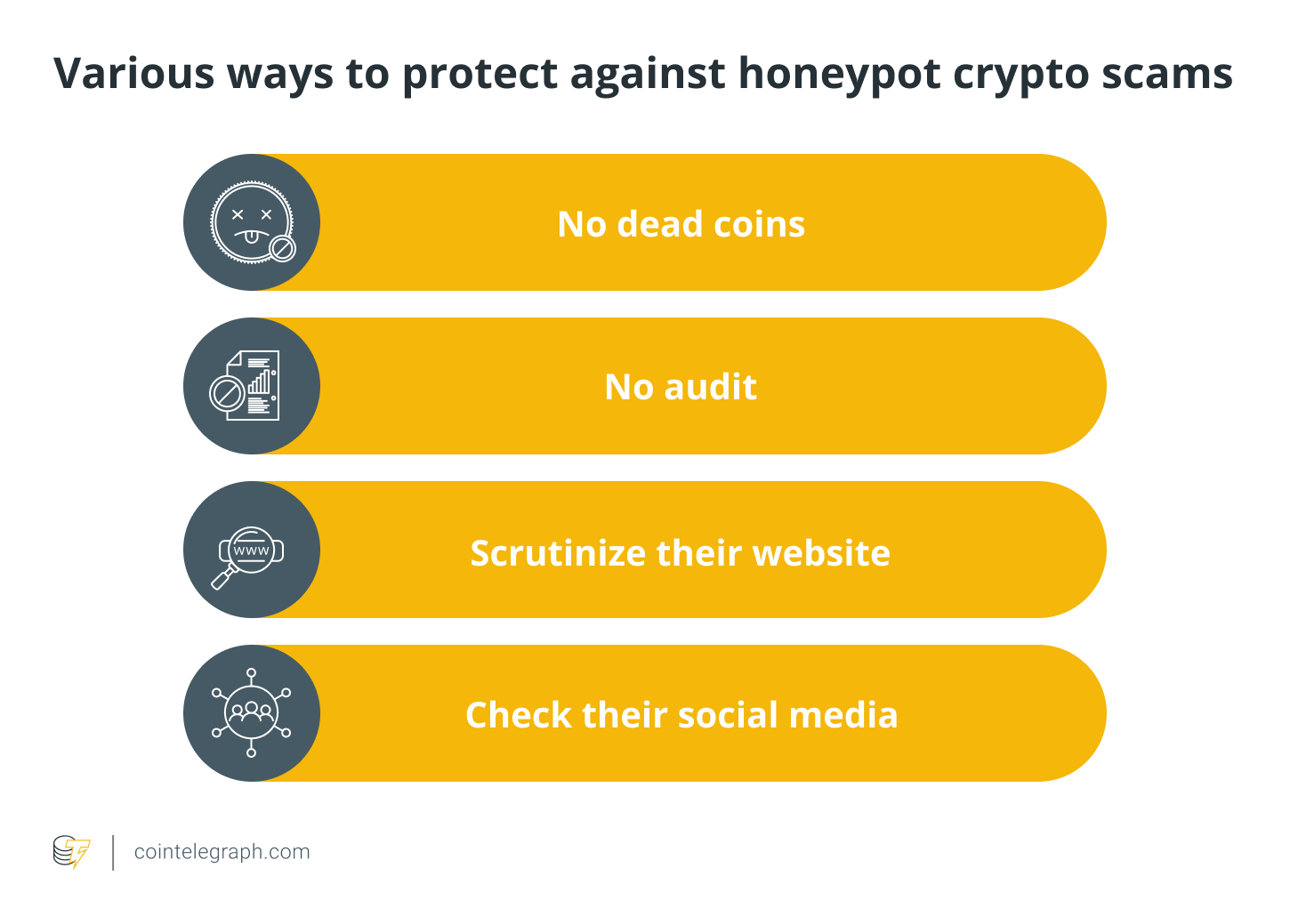
How to protect against honeypot contract scams?
This section guides how to get out of the honeypot scams to avoid losing your money. There are tools available to assist you in seeing red signals and avoiding these currencies. For instance, use Etherscan if the coin you’re buying is on the Ethereum network or use BscScan if the coin under consideration is on the Binance Smart Chain.
Find out your coin’s Token ID and enter it on the appropriate website. Go to “Token Tracker” on the next page. A tab labeled “Holders” will appear. You can see all of the wallets that hold tokens and the liquidity pools there. Unfortunately, there are numerous combinations of items of which to be aware. The following are some of the red flags that you should know to protect against honeypot crypto scams:
Token Sniffer is another excellent resource to spot honeypot crypto. Look for the “Automated Contract Audit” results by entering the Token ID in the top right corner. Stay away from the project if there are any alerts. Because many projects now employ contract templates, the “No prior similar token contracts” indication can be a false positive.
If your coin is listed on the Binance Smart Chain, go to PooCoin, enter the Token ID again and monitor the charts. Stay away if there aren’t any wallets selling or if only one or two wallets are selling your chosen coin. Most likely, it’s a honeypot. It’s not a honeypot if many wallets are selling the chosen coin. Lastly, you should conduct thorough research before parting with your hard-earned cash when purchasing cryptocurrencies.
How is a honeypot different from a honeynet?
A honeynet is a network made up of two or more honeypots. It can be beneficial to have a honeypot network that is connected. It allows businesses to track how an attacker interacts with a single resource or network point and how an invader moves between network points and interacts with many points at once.
The goal is to persuade hackers that they have successfully breached the network; therefore, adding more false network locations to the realism of the arrangement. Honeypots and honeynets with more advanced implementations, such as next-generation firewalls, intrusion detection systems (IDSes), and secure web gateways, are referred to as deception technology. Intrusion detection systems refer to a device or software program that watches for hostile activity or policy breaches on a network. Automated capabilities of deception technology allow a honeypot to respond to potential attackers in real-time.
Honeypots can assist firms in keeping up with the ever-changing risk landscape as cyber threats emerge. Honeypots provide vital information to ensure an organization is prepared and are possibly the best means to catch an attacker in the act, even though it is impossible to forecast and prevent every attack. They’re also a good source of knowledge for cybersecurity professionals.
What are the pros and cons of honeypots?
Honeypots collect data from genuine attacks and other illicit activity, giving analysts a wealth of knowledge. Furthermore, there are fewer false positives. For example, ordinary cybersecurity detection systems can generate many false positives, but a honeypot minimizes the number of false positives because genuine users have no motive to contact the honeypot.
Additionally, honeypots are worthwhile investments since they only interact with harmful actions and do not demand high-performance resources to process enormous volumes of network data in search of attacks. Lastly, even if an attacker is using encryption, honeypots can detect malicious activities.
Although honeypots provide many advantages, they also have a lot of drawbacks and risks. For instance, honeypots only collect data in the event of an attack. There have been no attempts to access the honeypot; thus, no data exists to examine the attack.
Furthermore, malicious traffic acquired by the honeypot network is only collected when an attack is launched against it; if an attacker suspects a network is a honeypot, they will avoid it.
Honeypots are generally recognizable from legal production systems, which implies that skilled hackers can easily distinguish a production system from a honeypot system using system fingerprinting techniques.
Despite the fact that honeypots are isolated from the real network, they eventually connect in some way to allow administrators to access the data they hold. Because it seeks to lure hackers to get root access, a high-interaction honeypot is often deemed riskier than a low-interaction one.
Overall, honeypots aid researchers in understanding risks in network systems, but they should not be used in place of standard IDS. For example, if a honeypot isn’t set up correctly, it might be exploited to acquire access to real-world systems or a launchpad for assaults on other systems.







Leave A Comment